
There have been unprecedented advancements made in the integration of IT tools for better management and more effective operation of critical industrial systems providing full connectivity for real-time control and management. Simultaneously, these innovations have also exposed the industrial environment to new modern cyber threats to operations and essential public services posing a real and substantial danger.
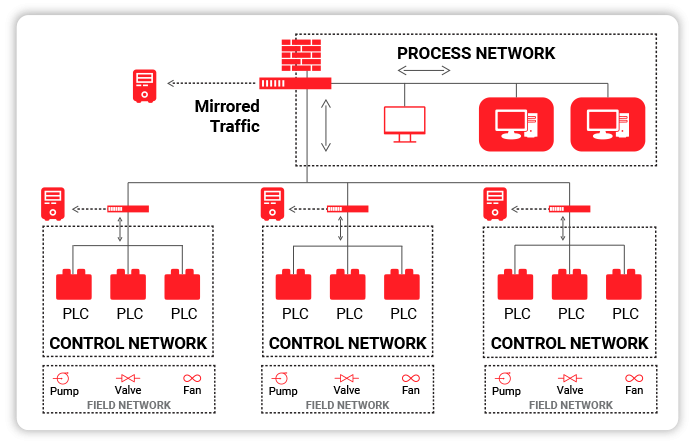
Investigate suspicious behavior and policy violations.
Alerts on attack attempts based on both signal and anomaly-based detection.

Performs asset discovery (the system passively maps the network) and detects the functionality of critical important assets within the control system environment.
Maximize the uptime of critical subsystems.